Microsoft 365 Data Loss Prevention: Guide to Data Protection and Compliance

Microsoft 365 Data Loss Prevention and Compliance setup guide
Organizations have sensitive information that they must protect and control access to, their use, and transmission. Data in organizations can include phone numbers, financial data, email addresses, health records, proprietary data, credit card numbers, etc. Organizations using Microsoft 365 can use Microsoft 365 data loss protection to protect and secure their data. Why?
Organizations need dedicated data protection solutions to protect the data and reduce their risk of loss by unauthorized access or inappropriate sharing. This practice, tools, and activities are called data loss prevention (DLP). It identifies, monitors, and protects sensitive business data from malicious activities, breaches, mishandling, and hacking.
This post shares the three main types of data loss prevention in Microsoft 365 and how to set up Microsoft 365's DLP. Learn how to set up Microsoft 365 DLP.
First, What is Data Loss Prevention?
Data Loss Prevention (DLP) (or data leak prevention) combines processes, tools, and strategies that prevent unauthorized access to, mishandling, and sharing of an organization's sensitive data.

How does DLP Work?
DLP in Microsoft 365 identifies, monitors, and protects sensitive data through deep content analysis across:
- Microsoft 365 services: Teams, SharePoint, Exchange, and OneDrive
- Office applications: Word, Excel, and PowerPoint
- Operating system endpoints: Windows 10, Windows 11, and macOS (Catalina 10.15 and higher)
- Non-Microsoft cloud apps

Individuals/organizations can break down DLP into two actions:
- Identifying sensitive data that needs protection
- Using DLP tools and software to monitor and prevent data breaches, malware attacks, or other types of hacking methods
DLP technologies/tools provide data protection in 3 ways: Data while at rest, in use, and in motion.
Here's what this means:
- Data in Use. This is data that an employee is currently working on or with. Protecting data in use involves tools/steps to authenticate and control user access to data actively being processed in apps or endpoints.
- Data in Motion. This is data that is 'traveling' from one point to another either over the network or in devices. Protecting data in motion involves encrypting it or using email/messaging security tools to prevent its access or sharing while it is being transmitted.
- Data at Rest. This is data under storage. Organizations store a lot of data that needs protection. Protecting data at rest involves using access control, encryption, or data retention to protect the organization's databases, cloud, endpoint devices, or other storage mediums.
Why is DLP important?
Unfortunately, we’re in a digital world full of hackers and bad actors trying to access information that isn’t theirs or that they’re unauthorized to access. And these cybercriminals and bad actors are becoming smarter, as 450,000 new types of malware appear daily on the internet, endangering individuals' and businesses' data.
So, understanding DLP can potentially keep your business from falling victim to malicious software and data loss.
Data loss prevention helps in the following ways:
- Data protection: Keeping your sensitive/private data out of the hands of bad actors, unauthorized access, and cyber criminals.
- Network security: Incorporating a DLP plan into your network can help protect your main network and connected devices.
- IoT device security: The internet of things (IoT) devices are much safer when protected by things like antivirus software and guest networks that help keep your data hidden.
- Compliance: Though regulations can vary by industry, country, state, or region, most businesses must comply with mandatory data protection standards, regulating how they organize, store and protect their customers’ data.
- Intellectual property: When a company’s network is vulnerable to hackers, it’s a risk to their trade secrets and business strategies being released to the public.
- Data transparency: For an enterprise to protect its data, it must know where data is stored, who has access, and for what purpose. This helps to identify weak points and eliminate unnecessary risks.
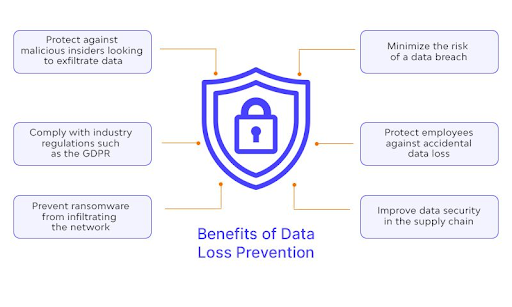
What are the Common Causes of Data Loss
A business can lose sensitive information in different ways: misplaced or hijacked data. Here are 4 common causes of data loss:
- Malware and viruses. Cause the majority of corporate and personal data loss. These attacks often begin with phishing emails embedded with malicious links infecting computers.
- Accidental data exposure. Corporate data breaches can occur due to people accessing information over unsafe devices or networks such as public Wi-Fi.
- Software malfunctions. Unexpected software malfunctions, such as shutdowns, may sometimes be out of the user’s control but can result in massive data loss. When a system randomly quits and closes its applications without warning, resulting in a reboot, it can be a hacker accessing information.
- Insider threats and hackers. This involves using compromised credentials to access user accounts to steal company information. This could result in serious incidents like identity theft or data exposure.
What are the Types of Data Loss Prevention in a Business?
There are 3 types of data loss prevention:
- Network DLP
- Endpoint DLP
- Storage and Cloud DLP
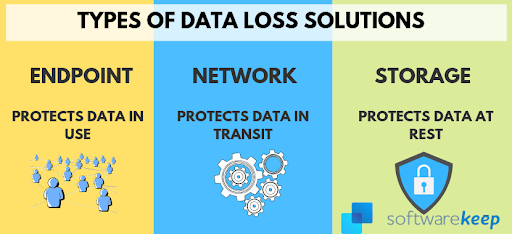
Let's discuss them in detail below:
Network Data Loss Prevention
In business, Network DLP gives you visibility into the company's network, allowing monitoring and control of information flow through the company's network/Wi-Fi, web, ISP, email, and/or Bluetooth. You can use network DPL to analyze your network's traffic and implement network security policies to prevent network-related data loss risks.
Businesses use network protection policies as Network DLPs to protect them from network-related data loss. Examples of network DPL are auditing, allowing, blocking, quarantining, flagging, or encrypting suspicious network activities.
Endpoint Data Loss Prevention
An endpoint is a computing device (often remote) that communicates back and forth with a network or other device to which it is connected. Examples of endpoints include:
- Devices like desktops, printers, Laptops, mobile devices (smartphones/tablets), etc.
- Workstations
- Servers
- Internet-of-things (IoT) devices
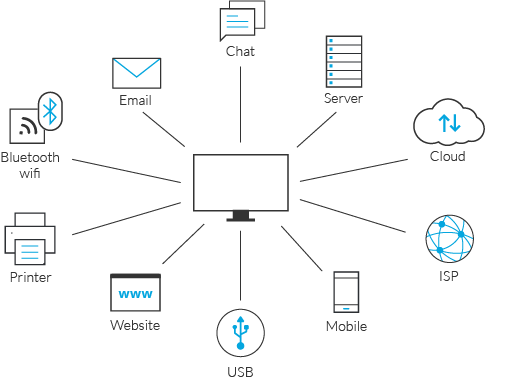
Endpoint DLP involves monitoring and protecting a company's endpoints used to store, access, or move its data and sensitive information. Endpoints are key vulnerable points of entry for threats and cybercriminals. In the U.S., 76% of staff gain inappropriate access to company-sensitive data through different endpoints.
Objectives for threats and cyber attackers targeting endpoints may include:
- Use it as an entry-and-exit point into an organization's network to access its data, information, and high-value assets.
- Access assets/data on the endpoint to hold hostage or exfiltrate for disruption or ransom.
- Take control of an organization's device/endpoint and use it to execute a DoS attack.
Endpoint DLP helps prevent the access and possible loss, misuse, and potential sharing of these sensitive data by unauthorized persons.
Modern enterprise endpoint security solutions are more behavior-centric today, incorporating a wide array of capabilities, such as exploit protection, antivirus, endpoint detection and response (EDR), device control, and analytics. Enterprise endpoint security strategies like in Microsoft 365 combine EDR solutions and endpoint protection platforms (EPP) with network and cloud security tools. This allows them visibility into many "unmanaged" network-connected devices, such as many IoT devices.
Cloud Data Loss Prevention (Cloud-based DPL)
Cloud DLP solutions protect enterprises that have adopted cloud storage. They help businesses protect cloud-based data and applications from leaks, unauthorized access, mishandling, or loss. It encrypts the data, ensuring that only cloud-authorized apps and persons can access it.

Cloud DLP also ensures that sensitive data isn't uploaded into the cloud without being first encrypted and only accessed by or sent to the company's authorized cloud applications.
Many Cloud DLP solutions can identify, classify, modify, or remove confidential data from an endpoint before sharing it to the cloud. This protects the data from malicious insider threats, cloud cyber threats, and accidental/unsafe data exposure.
Read: Datacenter & Virtual Machines: How do they work?
Microsoft 365 Data Loss Prevention
Microsoft 365 DLP, a component of Microsoft 365 Compliance tools, is used to protect data in Microsoft 365 (at rest, in use, and in motion). Microsoft 365 Compliance also includes Microsoft Information Protection (MIP) tools and capabilities that help in data protection and loss prevention.
You can apply Microsoft 365 DLP policies to data at rest, data in use, and data in motion in different locations, such as:
- OneDrive accounts, Exchange and SharePoint Online
- Teams chat and channel messages
- Microsoft Defender for Cloud Apps
- On-premises repositories
- PowerBI sites

Microsoft 365 DPL requires users/organizations to create data rules and policies categorizing data into different types, such as critical, sensitive, or confidential. It also allows customization to protect specific enterprise information and sensitive data.
Microsoft 365 DPL requires users/organizations to create data rules and policies categorizing data into different types, such as critical, sensitive, or confidential. It also allows customization to protect specific enterprise information and sensitive data.
By implementing Microsoft 365 DLP policies, enterprise/I.T. personnel can control actions on sensitive enterprise information. For instance, Microsoft 365 can block unauthorized access to sensitive data depending on the organization's data policies. But it can also be customized to send specific notifications when someone tries to undertake unauthorized data access, violating set rules.
In general, Microsoft 365 DLP can help enterprises/users undertake DPL in the following ways:
- Warn users/staff from inappropriate information sharing. Microsoft 365 DPL displays a pop-up policy tip when users try to share sensitive data or company information.
- Block staff/users from (or allow them to) share sensitive data/information. Users can do this through override customization and record justification.
- Hide/secure company sensitive data/info by locking and moving the info/data (data at rest) to an isolated, secure location.
- Hide sensitive information that shouldn't be visible to everyone in Teams chat or Microsoft Teams.
Office 365 Plans with Data Loss Prevention?

Microsoft 365 has DPL on different apps such as SharePoint Online, Exchange Online, and OneDrive for Business.
The DPL in these apps is available for 5 Microsoft 365 plans/licenses:
- Microsoft 365 Business
- Microsoft 365 A1/E3/A3
- Microsoft 365 E3/A3
- Microsoft 365 E5/A5/G5
- Microsoft 365 E5/A5/G5
(You can replace Office 365 with Microsoft 365 (new) for the abovementioned plans.)
The availability of Microsoft 365 DPL also includes files shared through M.S. Teams because Teams uses SharePoint Online and OneDrive to share files. Also, to get support for DLP protection in Teams Chat, one needs an Office 365 E5 license.
How to Set Up DLP in Microsoft 365: Step-By-Step Process
Setting up Microsoft 365 DLP is relatively simple because of its built-in features and functionalities.
The steps below will guide you in the process:
Step 1: Log in to your Microsoft 365 admin center
- Log in to your Microsoft 365 admin center with the authorized credentials.
- Navigate to the Security & Compliance Center tab.
This is where you'll undertake all the Microsoft 365 DLP setup.
Step #2: Select Prefered DLP
- Navigate the Security and Compliance Center > then click the Data Loss Prevention Tab.
- In the new window, click Policy.
- A new window will pop up.
Step #3: Create & store DLP policy(s)
- In the new window, click +Create a policy.
- This will direct you to a new window named: New DLP policy.
Step #4: See Templates
- The New DLP policy window will present you with various templates/wizards to help you create different policies, including medical, financial, privacy, and customized situations.
- Now, select from the list of policy templates to set up or choose to customize your own policy.
- For example, to create a HIPPA policy: ChooseMedical & Health > U.S. Health Insurance Act > Click Next.
- Choose a template/standard relevant to your business and follow the on-screen guidelines.
Sep #5: DPL Name & Description
- Under Name Your Policy tab, give the Policy a name
- Provide a policy description that matches your (enterprise) needs.
- Click the Next button.
Step #6: Choose Locations
- Next, choose the locations where the new Policy will be active or specify where you want that Policy to be enforced.
- Microsoft 365 allows you to specify whether you want all locations or a specific location: Click "specify where you want that policy to be enforced."
- Examples of specific DPL locations in Microsoft 365 or Sharepoint, Exchange Online, or OneDrive.
Step #7: Policy settings — Customize the Content type to protect
- Microsoft 365 DLP setup allows you to choose different kinds of settings for the content type to protect:
- Simple settings: applies default/pre-existing Microsoft 365 DLP rules.
- Advanced settings: creates a new rule(s) for stricter policies, including exceptions, user notifications, user overrides, incident reports, or actions to take when conditions are met.
- You can also get more granular with the settings in different aspects, like content, staging, and actions.
- Review your settings/rules, then click the Create button.
Step #8: Turn on Microsoft 365 DLP Policy & Save settings
- Finally, check and turn on your newly created Microsoft 365 DLP Policy right away.
- You can also test it first to see if it's working according to your wish.
- Microsoft 365 also allows you to keep it turned off.
- One last thing: click Save to save all your settings.
Voila! You can celebrate.
Step #9: One more thing — Microsoft 365 DLP Reporting
After creating your Microsoft 365 DLP policies and turning it on, check and verify that it's working as intended.
Do this by checking the DLP reports and viewing the number of DLP policies and rule matches over time. This will also give you a view into the number of overrides and any existing false positives.
The Microsoft 365 DLP reports show broad trends over time and give specific insights into:
- DLP Policy Matches over time and filter by date range, location, policy, or action
- DLP incident matches also shows matches over time, but pivots on the items rather than the policy rules.
- DLP false positives and overrides shows the count of false positives and, if configured, user overrides along with the user justification.
You can take the opportunity also to set up recurring Microsoft 365 DLP reports.
6 Data Loss Prevention Best Practices For Businesses
Businesses should prioritize protecting their data, which is essential to daily operations. Here are DLP best practices to help enterprises create a safe environment to house and use their data.

#1. Know the 3 types of data loss prevention
Before deciding on a DLP procedure for your business, understand the types of data loss prevention for businesses. Generally, there are three types of data loss prevention for businesses:
- Network DLP
- Endpoint DLP
- Cloud DLP
Once you identify this, select the best service for your business.
#2. Identify and classify your data
The data running throughout your enterprise isn’t the same. To protect your data, first, know what kind of data your business has and uses for operations. Examples of data can be:
- Financial records
- Phone logs
- Customer information such as names and email addresses.
- Medical and health information
- Privacy
- Custom
- And more.
You’ll also need to categorize this data based on its level of importance to prioritize sensitive information that needs protection.
#3. Implement a strong DLP policy
DLP policies, like Microsoft 365 DLP, outline how the business can protect, store, and share its data. A business implements these rules and procedures throughout its storage, cloud, and network. An example of DLP may include prohibiting sharing or distribution of information outside of the established network. This can protect your network/data from internal and external threats.
#4. Hire experienced IT personnel
To have and maintain a successful DLP policy, you need experienced professionals with skills in dealing with DLP risk analysis, data breach reporting, and data protection law. This will protect your business and analyze your networks for potential threats.
#5. Educate employees about DLP
Data loss prevention is an ongoing process. Since employees are critical players in the company, they’re also critical players in the success of DLP in a business. Educating your staff on DLP policies, new DLP software, DLP procedures, and rules can help streamline your entire data protection. This will also help everyone in the business know how the company is legally required to handle the data it stores and uses.
#6. Back up your data
There’s almost nothing worse than having a computer shutdown that wipes out your important data. But sometimes these things are out of your control. You should back up your data to reduce the chances of your information getting lost. You can back up the data in the cloud, external hard drive, or removable media device.
In Conclusion
DLP is one of Microsoft Purview tools that protects sensitive enterprise items wherever staff live or travel. Businesses seeking robust data security can use Microsoft 365's DLP as a significant first step. With data loss prevention, users/staff cannot send or share sensitive information outside the company domain or to public cloud storage like Google Drive. It blocks and logs any accidental or malicious attempt to access or send this information out of the network.
Are you looking for more tips? Check out our other guides in our Blog or visit our Help Center for a wealth of information on how to troubleshoot various issues.
Sign up for our newsletter and access our blog posts, promotions, and discount codes early. Plus, you'll be the first to know about our latest guides, deals, and other exciting updates!
Related Articles
» How to Keep Your Data Safe When Using Microsoft Office 365
» Mobile Device Management (MDM) for Microsoft 365: Ultimate Guide
» Why You Should Block Microsoft Legacy Authentication
» Step by Step Guide to Set Up Office 365 Business eMail
» How to fix the 'We couldn't create the Outlook data file' error











