An In-Depth Guide to Cloud Security

As cloud computing becomes widely accepted, cloud security is becoming more significant in organizations worldwide. Almost all organizations, be it software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS), use cloud services to cater to their complex security problems.
Being shared resources, cloud systems are accessible via the internet, which makes them vulnerable to malicious attackers. In recent years, numerous high-profile security attacks resulted from misconfigured cloud systems. Due to this, attackers had convenient access to confidential information.
Traditional security measures are falling short in this ever-evolving world of cloud security. Cloud security needs to be addressed with a different approach.
Organizations are now being offered new security tools, like Cloud Security Posture Management (CSPM) and Security Information and Event Management (SIEM), to enhance their visibility over cloud environments, identify gaps in security, and proactively rectify them.
Introduction to Cloud Security
Cloud security is a collection of technologies and services to safeguard sensitive business-critical online data from theft, deletion, and leakage.
Cloud security mainly focuses on the following:
- Providing privacy of data across different networks
- Catering to all cybersecurity concerns of the business
- Controlling the access of users, devices, and software
Numerous protective methods can help secure the cloud, including firewalls, access control, virtual private networks (VPN), not using public internet connections, penetration testing, obfuscation, tokenization, and many more.
What is Cloud Security?
Cloud security is a collection of procedures and technology designed to address external and internal threats to business digital security. Organizations need cloud security as they move toward digital transformation and incorporate cloud-based tools and services into their infrastructure.
Cloud security is an important part of cloud computing.
What is cloud computing?
The "cloud" or, specifically, "cloud computing" refers to the process of accessing software, databases, and resources over the Internet and outside the confines of local hardware restrictions.
It gives organizations flexibility when scaling their operations by offloading a portion, or majority, of their infrastructure management to third-party hosting providers.
The common and widely adopted cloud computing services are:
- IaaS (Infrastructure-as-a-Service): A hybrid approach where organizations can manage some of their data and applications on-premise while relying on cloud providers to manage servers, hardware, networking, virtualization, and storage needs.
- PaaS (Platform-as-a-Service): Gives organizations the ability to streamline their application development and delivery by providing a custom application framework that automatically manages operating systems, software updates, storage, and supporting infrastructure in the cloud.
- SaaS (Software-as-a-Service): Cloud-based software hosted online and typically available on a subscription basis. Third-party providers manage all potential technical issues, such as data, middleware, servers, and storage, minimizing IT resource expenditures and streamlining maintenance and support functions.
Principles of Cloud Security Architecture
A cloud security system’s architecture is the layout that connects all the elements required to protect cloud resources against internal and external security threats. Here are some core principles of cloud security architecture:
Network Security
Cloud network security operates on a shared responsibility model. Here the organizations are responsible for securing traffic flows to and from cloud resources. They are also responsible for exchanges between the public cloud and on-premise networks. Efficiently segmenting networks play an important role in limiting an attacker's lateral movement once they have gained unauthorized access to a network.
Security by Design
Cloud architecture needs to be designed to mitigate vulnerabilities caused by security misconfigurations. Such as, when an organization is handling sensitive data on the cloud, external access to it should be locked, and no administrator should be able to open access to the public internet. This will ensure robust data protection.
Visibility
Organizations are known for using multi-cloud and hybrid-cloud deployments, as traditional security services often fail to provide full-proof protection.
An effective cloud security strategy ensures that the layout is leveraged to enable them to promote visibility throughout a cloud-based infrastructure in any organization.
Solutions like SolarWinds’ full-stack observability toolkit can provide oversight for hybrid cloud configurations, keeping tabs on a combination of in-house and remotely hosted assets.
Physical and virtual hosts alike can be encompassed by the latest platforms designed to protect against many modern threats. This makes threat detection in particular, easier to implement and automate for improved agility.
Automation
Automation plays a critical role in swiftly provisioning and updating security controls in an organization’s cloud environment. Furthermore, automation can be valuable as it helps identify and promptly remediate real-time misconfigurations and other security gaps.
Agility
The cloud facilitates the swift development and deployment of innovative solutions. Organizations can adopt cloud-native security solutions to ensure seamless integration into the agile development lifecycle.
Unified Management
In most organizations, security teams are often overworked and have limited resources at their disposal. That's why cloud security solutions should offer unified management interfaces, which enable teams to oversee numerous cloud security measures from a single dashboard centrally.
This approach would streamline operations and increase cloud security management efficiency.
Understanding Different Cloud Security Deployment Models
The different kinds of cloud security deployment models are identified based on ownership, scale, cloud nature, purpose, and access.

The deployment model will also determine the location of the organization's servers and the administrator who will be in control.
Different types of cloud computing deployment models are:
- Private Cloud: The infrastructure and resources are dedicated to a single organization. Amazon Web Services, Microsoft Azure, Google Cloud Platform, Dell, and Cisco offer private clouds.
- Public Cloud: This is opted for by companies with low-security issues as the cloud is available for the general public under the pay-as-you-go model. Public clouds are provided by Amazon EC2, Google App Engine, Microsoft Azure, and IBM Cloud.
- Community Cloud: The cloud is shared by multiple organizations, usually with the same background. Companies like Microsoft, Oracle, Amazon, IBM, and Google offer community clouds.
- Hybrid Cloud: Partly managed by service providers and partly by the organization, it combines private and public cloud.
Cloud Security Services and Solutions
The following are the most commonly key cloud security services and solutions to help organizations effectively protect their cloud computing environments.
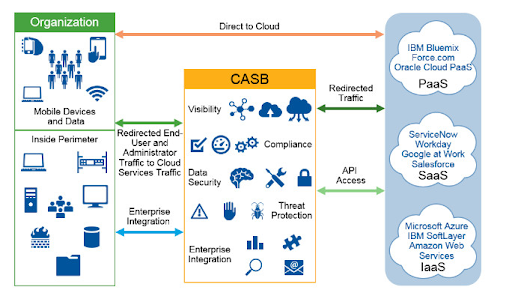
Cloud Access Security Broker (CASB)
Acting as a gateway between cloud users and service providers, CASB can be integrated as a software application or a physical device, which can be installed on-premises or in the cloud.
CASB solutions help organizations enforce security policies, detect potential threats, and monitor real-time user. CASBs also offer data encryption and malware protection.
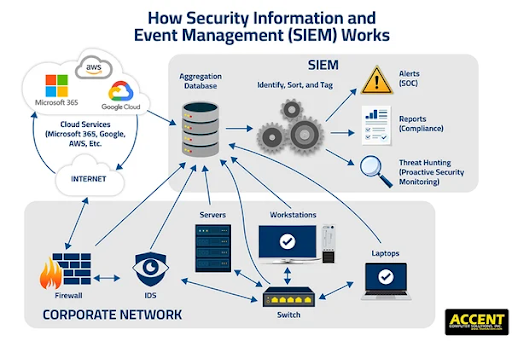
Security Information and Event Management (SIEM)
Uniquely capable of providing centralized log management and analysis, SIEM solutions allow organizations to detect, investigate, and respond to cyberattacks more effectively.
SIEMs collect security event data from various cloud resources and enable the identification and elimination of potential security breaches.
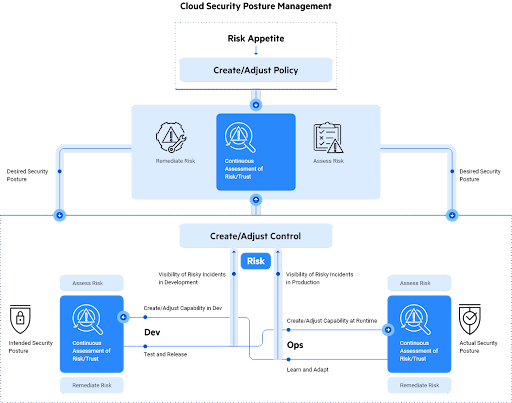
Cloud Security Posture Management (CSPM)
By scanning cloud configurations, CSPM tools identify security misconfigurations and vulnerabilities.
Alongside reporting on cloud configurations for compliance purposes, CSPM tools can also spot misconfigurations and automatically mitigate risks.
Cloud Workload Protection Platform (CWPP)
CWPP solutions can safeguard cloud workloads by increasing resource visibility across multiple clouds and ensuring proper cloud deployment.
CWPP tools are proficient at security tasks like scanning and mitigating vulnerabilities, hardening operating systems and applications, performing integrity checks, and whitelisting applications.
Cloud and Compliance
Cloud environments must have an additional streak of privacy and associated security implications. Compliance with different regulatory requirements like HIPAA, SOC 2, PCI, and other internal requirements is becoming increasingly complex.
Strict adherence to such security and privacy standards requires legal compliance and an efficient risk-management strategy for your cloud environment.
Automating and implementing policies and other controls is one way to ensure compliance. This includes handling policies for tracking, prioritizing, and eliminating risks against important business systems, role-based access controls, policies for securing data, safe user behavior policies, and the use of encryption.
Cloud Security Best Practices
As per a 2022 study on cloud data security, more than 50% of organizations reported a breach in their cloud environment.
There will be some risks in moving and securing your data on a cloud. However, this means that you need to leverage its varied security benefits.
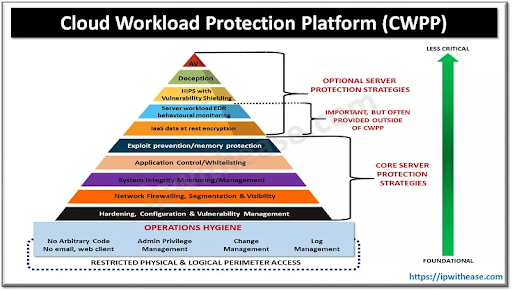
Image Source: Spiceworks
To counter these risks, businesses should follow the best practices recommended by industry experts.
- Segment and isolate the system: Divide the system into zones. Use each zone to isolate applications, containers, instances, and corresponding data stores.
- Ensure identity access management hygiene: This is important for blocking security problems arising due to hackers or negligence.
- Maintain proper lifecycles: As the creation in the cloud gets easier, organizations often spin new instances, and the old ones are abandoned. These abandoned instances are left unmonitored even though they are active. Hence, proper commissioning and decommissioning of instances is required to protect the data.
- Configure beyond the default: You might find a generous default configuration on cloud services. It is recommended to change these configuration policies as they may open you up to unnecessary risks.
- Perform vulnerability scans regularly: Security audits are one of the biggest parts of cloud security. They must be thorough and regular as they can identify a problem before any attacker can take advantage of it.
Cloud Security Trends for 2023
With the ever-changing cloud technology space, organizations must stay updated about the latest trends to counter cloud-based breaches. Here are some trends that can change the cloud security landscape in 2023:
- More focus on IaaS attacks as more companies move their infrastructure to the cloud.
- Cloud-based infrastructure to deliver malware may see a boom as hackers are expected to host malware as a service (MaaS) platforms.
- Targeted campaigns may focus on cloud-based attacks as hackers become more savvy to maintain their foothold in victim networks.
- As organizations opt for multi-cloud security, awareness around a comprehensive multi-cloud security strategy will increase.
Wrapping up
In modern business, cloud security plays an integral part. Hence, organizations are increasingly embracing cloud security in their overall business strategy.
Companies use combined technologies and train their staff to accept and adopt cloud security. As this realm of cloud security evolves, keeping in touch with the latest trends and best practices will help you maintain a secure cloud environment.











